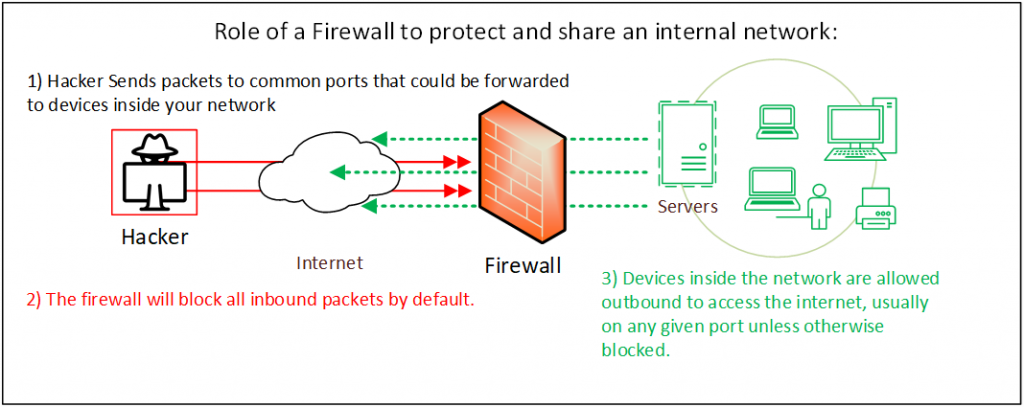
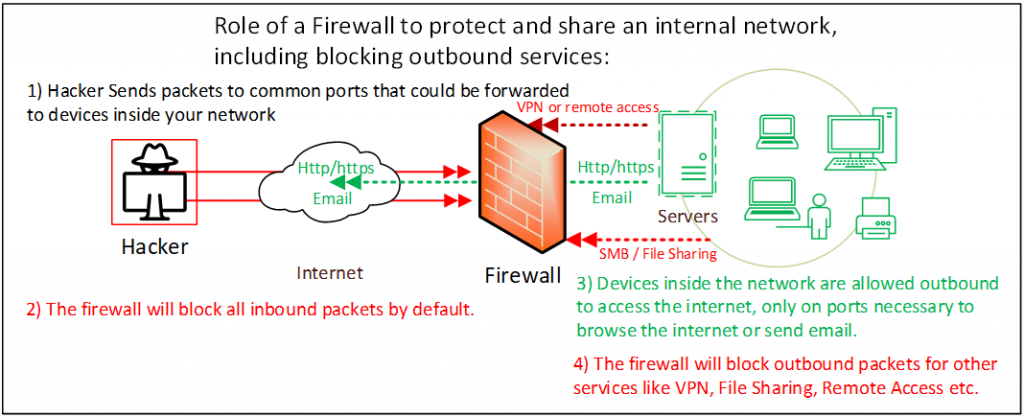
The dangers of using USB devices in your computer, especially if from an untrusted source, can bring about two main threats to your business:
1. Data Leakage
Allowing anybody to use disk drives on your business computers provides staff with a way to extract data without being detected too easily.
Your entire portfolio of secrets, protected intellectual property, financial spreadsheets, backups… anything available to users on the network can be stolen.
You can enable logging in the event viewer but you still need to catch the event or suspect it has happened. But it’s too late once it’s taken.
2. Malware or System/Network compromise
Autoplay on computers will load software that has been preinstalled on the USB drive. If the payload is malware or a virus then it will infect your machine and potentially any computers on the same network.
Your logged in credentials could be stolen and your identity easily compromised. Furthermore if the device is a server or something stationary like a desktop then there are devices that allow remote access to the monitor, keyboard and mouse.
Think carefully if you are going to allow USB drives to be used on your computers. If you are make sure it’s only to a set of privileged users and enable logging where relevant.